Topic Content
Network Security
Not only does an organization have to worry about its internal network securities on its systems of intranet etc it has to be aware of the securities concerning the network when it comes to the internet and external individuals who have destructive or criminal intent. Securing large computer networks requires specialized security. Three common technologies commonly used to ensure network securities are firewalls, intrusion detection systems, and virtual private networks, (O’Leary 2017, p211).
- Firewall – hardware and software controlling access to a company’s intranet and other internal networks. Most use software or a special computer called a proxy server. Communications between the internal networks and the outside world pass through this server, which decides after evaluation of the source whether or not the particular message or file should pass in or out of the organizations network, (O’Leary 2017, p211).
- Intrusion detection systems (IDS) – works with firewalls to protect the network. Uses sophisticated statistical techniques to analyse incoming and outgoing traffic and can recognise signs of network attack and disable access before the intruder can do damage, (O’Leary 2017, p211).
- Virtual private networks (VPN) – creates a secure private connection between the internal network and remote users. Special VPN protocols use encryptions to secure a dedicated line between the user and network and make s it appear as if the workstation is located on the corporate network, (O’Leary 2017, p211).
Cyber adversaries are aggressive and persistent in their efforts to compromise networks and information.They are constantly improving their tradecraft in an attempt to defeat our network defences and exploit new technologies, targeting the weakest link and if the network security of their primary target is robust, they will move to more easily compromised connected networks that could provide access to the primary target (Commonwealth of Australia 2016).
Costs as a result of cyber attack will be a major concern to organizations and constant watch on cyber security and the drivers which increase network vulnerability is required. There are specific drivers of the rising costs of malicious cyber activities, noted by the research done in 2016 for the creation of the Australian Cyber and Security Strategy :-
- Greater number of cyber security incidents
- Greater number of targets
- Greater sophistication
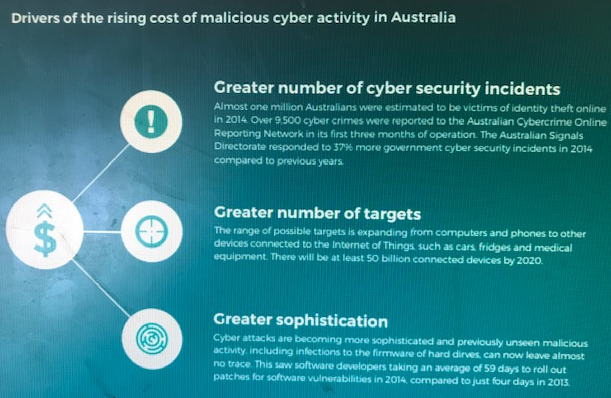
Source: Drivers of the rising costs of malicious activity, Commonwealth of Australia (2016)
Methods to prevent malicious cyber activity
The possible ten best ways to reduce Exploitable Weaknesses and Attacks (WaterISAC Security Information Center, 2015), is :-
- Maintain an Accurate Inventory of Control System Devices and Eliminate Any Exposure of this Equipment to External Networks
- Implement Network Segmentation and Apply Firewalls
- Use Secure Remote Access Methods
- Establish Role-Based Access Controls and Implement System Logging
- Use Only Strong Passwords, Change Default Passwords, and Consider Other Access Controls
- Maintain Awareness of Vulnerabilities and Implement Necessary Patches and Updates
- Develop and Enforce Policies on Mobile Devices
- Implement an Employee Cyber security Training Program
- Involve Executives in Cyber security
- Implement Measures for Detecting Compromises and Develop a Cyber security Incident Response Plan
Conclusion
I would think that the best way to ensure cyber security is implemented and maintained, is for a company to create a team which will provide targeted advice and support on cyber threats and vulnerabilities to the owners and operators of the company network.
Due to the increased use of the internet and the dangers to vulnerability to cyber attack it is reasonable to say that network security in organizations as well as on home networks has become a critical and prerequisite requirement. The general statistics which can be found in the numerous research done by various countries is testament to this assumption.